
There are several methods that viruses can use to spread. They take advantage of a weaknesses in computer programs or people. They may spread several ways.
- Viruses may be sent as an executable file in an email attachment and trick the recipient into clicking on it. To get the virus the user must run the executable attachment.
- Viruses may send themselves in an email attachment that is in a form which takes advantage of a weakness in a program running on the target computer, e.g, Adobe Flash Player, Microsoft Power Point, etc. To get the virus the user only needs to open the attachment.
- A virus may be sent as an HTML based email with code in it designed to take advantage of a vulnerability in the browser or email client to install itself onto the targeted computer system.
- Some viruses are on the boot sector of a floppy or disk drive. When the disk or floppy is placed in another computer, it will infect it. This type of virus is not as common today since email is a more popular form of sending files.
Methods of Disguise
Many viruses will disguise their files to look benign. For example they may name a file “yourinfo.exe.txt”. This naming method will take advantage of Microsoft’s default setting to hide file extensions of known types. Users may think this is a text file and double click on it which will cause it to run. Read How to Configure your Windows System to Show File Extensions All the Time to learn how to change Microsoft’s default settings to help guard against this weakness.
Many viruses will disguise their emails to look very official. It may appear that the email came from one of the following:
- A bank
- Microsoft
- Your stock broker
- eBay
- Paypal
- The Government

The email may contain an attachment which is zipped and requires a password to open. The password is given in the text of the email and the reader is told to unzip the attachment and read the attached file for complete information. The file may be in a zipped and password protected format, not to keep it confidential, but to prevent anti-virus programs that run on email servers from detecting the virus inside. The reader may be told one or more of the following to get them to read the attachment.
- You are in trouble
- You did something wrong
- You must apply this patch to prevent viruses
- You are infected by a virus and must run the attachment to remove the virus.
Faked Sender Address
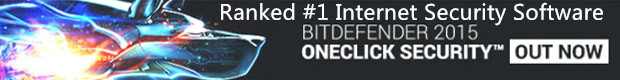
Viruses will almost always fake the sender of an email. It will make it look like the email came from someone like a friend, government agency, financial instution, or a legitimate computer security company to name a few possibilities. If the virus chooses to spread, faking as though it is a friend or long lost aquaintance, it may choose the sender name from the address book of an already infected victim as shown in the figure below.
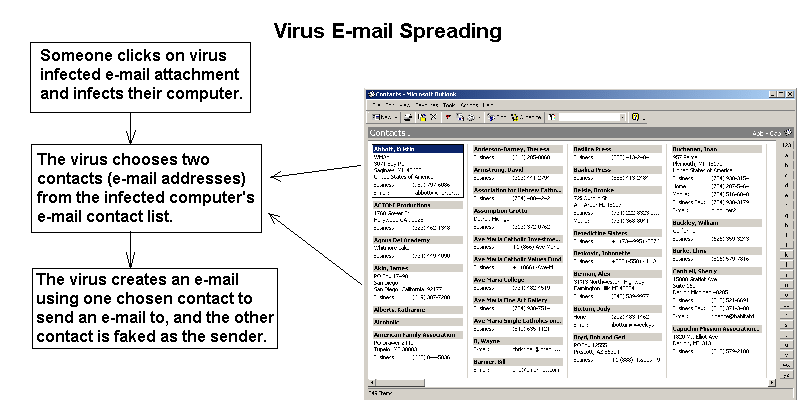
Be aware of the fact that viruses fake the sender of emails. Never open attachments unless you are sure of who the sender is and that the sender really sent the attachment.
Virus Actions
Once a virus has begun the infection process, it will perform several actions to preserve itself and propagate to other systems. These include one or more of:
- Attaching itself to a system file or some other file on the hard drive.
- Creating a new file with a copy of itself on the hard drive.
- Modifying the system registry so it is automatically run when the computer is booted.
- Some older viruses would write themselves into the boot partition (a special section of a hard or disk drive used to run a program required to boot a computer) of a computer.
- Scan the email address list of the infected computer and try to mail itself to people on the list. It may choose random people on the list to be spoofed as the sender. It may also send a copy of the address list to someone to add email addresses in the address list to spam lists.
- It may download and install other malware on the infected system such as a backdoor or hacker tool which may be used by a hacker to get control of the infected computer.
Virus Recognition Time Period
From the time a virus is released on the internet to the time your virus scanner can recognize it, the following phases occur:
- The virus is released on the internet and begins replicating across the internet to various systems.
- The virus is detected by someone. A virus scanner cannot detect the virus since there is not a matching definition for this new undiscovered virus.
- The virus is sent to the anti-virus program developers to develop a signature that can be used to recognize the virus.
- The anti-virus signature or footprint must be tested to be sure it does not mistake legitimate programs as virus programs (false positives).
- The new virus signature is added to the list of virus definitions in the anti-virus vendor database.
- Customers will periodically download the new definitions. There is a delay between when the anti-virus vendor database is updated and when the customer downloads the new definitions to their anti-virus program library list of viruses.
During the time between each of the above phases, the virus is still spreading and the systems running the anti-virus program are not protected against the virus until the end of the last phase. One reason it is important to do virus updates often is to cut down the time period between the last two phases and thus reduce the period of vulnerability. However there is still a significant period of time that the anti-virus program cannot protect aganist the virus. This is why user education is important so the user can prevent some infections. This is part of a layered defense stratege.
Interceptors
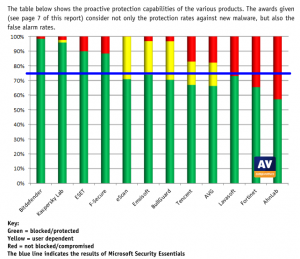
A second kind of virus scanner that recognized viruses or malware based on things they try to do rather than a footprint may catch unknown viruses, known as proactive defense. Some of these programs are called interceptors. They monitor system requests for actions that may be considered threating or hostile such as writing to the hard drive or system registry and may ask the computer user if the request should be allowed. An interceptor can detect other malware beyond viruses such as trojans.
Interceptors can be disabled by malware of viruses (so they should not be your only defense) and
they can be annoying to use since they may be constantly asking wether specific requests from specific programs are OK to allow.
Internet security suite with excellent proactive defense ablity is Bitdefender Internet Security, which ranked #1 in the famous Proactive/Behavioral Test 2014 by AV-Comparatives.
Other Malware Prevention Methods
There are other products that will look at the files on the computer and keep some basic information about them such as their size, last modification date, and other characteristics. These programs can determine whether system files and other files have been changed so they can possibly tell if malware or a hacker had made changes to a computer system. One integrity checker used commonly on Linux or Unix systems is called TripWire. An integrity checker by itself is not sufficient protection against malware since it cannot specifically recognize viruses or repair them. It can only recognize a system change.
